The core idea of asymmetric cryptography
Asymmetric cryptography or public key cryptography is a cryptographic system that uses a pair of keys (public key and private key) which are linked with mathematical dependencies. The more complex math algorithms are used the more difficult it is to crack the cypher. Ideally, the math problem should be so complex that guessing a solution or trying to break it would be literally impossible or unfeasible.

Public key
Public key can be freely distributed over open networks, Internet or sent via regular mail on the flash drive. It is linked mathematically with its corresponding private key.
Private key
Private key should always be kept secret from the public. Always. Secret. Within one cryptographic system private key is associated with one single user (one ID, number or username).
The idea of asymmetric cryptography is to make one way irreversible encryption and decryption operations. If a piece of data is encrypted with the public key, it can be decrypted only with the corresponding private key. If data is encrypted with the private key it may be decrypted only by public key matching the pair. It’s like a one-way-lock and one-way-unlock case.


Note from Wikipedia
Public key cryptography systems often rely on cryptographic algorithms based on mathematical problems that currently admit no efficient solution — particularly those inherent in certain integer factorization, discrete logarithm, and elliptic curve relationships. Public key algorithms, unlike symmetric key algorithms, do not require a secure channel for the initial exchange of one (or more) secret keys between the parties.
How it works
In asymmetric cryptographic systems each participants has own pair of keys. Public keys are freely distributed around the system while private keys are hidden secret. Asymmetric encryption eliminates man-in-the-middle attacks because intercepting only a public key is useless. It is the private key which keeps the secret private and hidden from prying eyes.
Examples of applications
Asymmetric encryption
Asymmetric encryption algorithms are built the way that data which is going to be sent is always encrypted with the recipient’s public key.

It can be unlocked (decrypted) only with recipient’s private key.
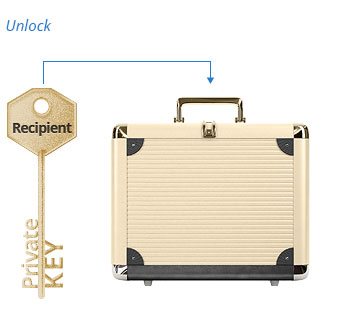
This model allows sending data securely, so that only intended receiver can read actual information.
Digital signatures
Digital signatures, unlike asymmetric encryption algorithms, are designed the way that data is encrypted only with the private key of data sender…

… and can be decrypted only with the sender’s public key.

This scheme ensures user authentication because only one single user owns the private key.
The big deal
In asymmetric encryption a reliable and efficient key management policy becomes crucial. To keep private key protected there may be used some passwords, pins or even biometric verification methods. Design of hardware which stores the private key should be resistant to tampers to extract the secret key. The big deal about asymmetric encryption is how to keep private key a real secret.
Don’t wait until it’s too late
Buy No.1 BC card
Card is required to encrypt voice calls, chats, file transfers and use No.1 BC: Mail
Find where to buyUse No.1 BC apps
Make sure to install the latest version of No.1 BC applications.